
Do you love Oreos? How about Pop-Tarts? Instant ramen?
Source: Gizmodo – Your Favorite Snacks May Be Driving Deforestation in Ancient Indonesian Peatlands


Do you love Oreos? How about Pop-Tarts? Instant ramen?
Source: Gizmodo – Your Favorite Snacks May Be Driving Deforestation in Ancient Indonesian Peatlands

The idea of making a sequel to one of the biggest animated films of all time somehow seems more than just “obvious.” “Essential” is likely a better word. And yet, the filmmakers behind Frozen and the upcoming Frozen II say making a sequel wasn’t their first instinct and the road to get there was more than a little…
Source: Gizmodo – Deciding to Make Frozen II Was Much More Complicated Than You’d Expect

A tuna salad sandwich is a simple pleasure. Canned fish, mayo, and maybe a little relish are all you really need, but some brands of canned fish can be bland and, once you add mayo, any flavor the tuna was bringing becomes super muted.
Source: LifeHacker – How to Add Umami to Tuna Salad
Creating an application clone on a smartphone is one way to open 2 different accounts for an application for certain purposes. Actually, cloning an application is not necessary when the application has a feature to open more than one account. Examples are Applications made by Google.
Source: LXer – Shelter, Application To Create An Isolated Space On Android!
Google and Amazon don’t have the warmest relationship, but they’ve been patching things up recently. Amazon reinstated support for YouTube on its Fire TV platform in July, while Google enabled Amazon Prime video streaming through Chromecast devices….
Source: Engadget – YouTube TV is now available on Amazon Fire TV devices

Enlarge / Sven Olaf Kamphuis’s Facebook profile picture, taken in front of the original CyberBunker facility. Its German successor was seized by police on September 26. (credit: Sven Olaf Kamphuis)
On September 26, a data center in a former NATO military bunker in the town of Traben-Trarbach, Germany was raided by police, according to a report by the Associated Press. Set up by a man who authorities describe as a 59-year-old Dutchman, the “CyberBunker” offered “bulletproof” hosting services—promising to keep hosted sites secure from law enforcement actions and operational regardless of legal demands.
According to authorities, the bunker housed the servers for a multitude of “dark web” sites selling drugs, hosting child pornography, and conducting other illegal activities. Among the sites hosted was “Wall Street Market,” which authorities claim was one of the world’s largest criminal marketplaces—selling drugs, stolen financial data, and hacking tools—until it was taken down earlier this year. The Traben-Trabach data center was also involved in a 2016 distributed denial of service (DDoS) attack against Deutsche Telekom.
Seven people were arrested, and six other suspects, including two Dutch nationals, are still being sought by police. The raid was part of a coordinated law enforcement action at five locations by authorities in Germany, the Netherlands, Poland, and Luxembourg.
Read 5 remaining paragraphs | Comments
Source: Ars Technica – German police seize “bulletproof” hosting data center in former NATO bunker

Last week, we discussed why it’s probably a bad idea to throw something in your recycling bin when you’re not sure if it’s recyclable. (When in doubt, throw it out!)
Source: LifeHacker – Make a Bin for All the Stuff You Don’t Know How to Recycle
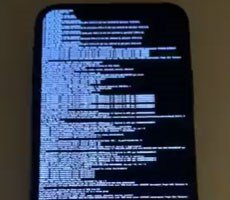
Over the weekend, news spread of an unpatchable “checkm8” exploit that could allow millions of iPhone users to quickly and easily jailbreak their handsets. Lest there was any doubt it works, the hacker who developed the exploit posted a video on Twitter showing checkm8 in action on an iPhone X running iOS 13.1.1.
The bad news for Apple
Source: Hot Hardware – Axi0mX Teases iPhone X Running iOS 13.1.1 Jailbroken With Checkm8 Exploit
Matthew Green, a cryptographer and professor at Johns Hopkins University, writes: So what did Snowden’s leaks really tell us? The brilliant thing about the Snowden leaks was that he didn’t tell us much of anything. He showed us. Most of the revelations came in the form of a Powerpoint slide deck, the misery of which somehow made it all more real. And despite all the revelation fatigue, the things he showed us were remarkable. I’m going to hit a few of the highlights from my perspective. Many are cryptography-related, just because that’s what this blog is about. Others tell a more basic story about how vulnerable our networks are.
“Collect it all”
Prior to Snowden, even surveillance-skeptics would probably concede that, yes, the NSA collects data on specific targets. But even the most paranoid observers were shocked by the sheer scale of what the NSA was actually doing out there. The Snowden revelations detailed several programs that were so astonishing in the breadth and scale of the data being collected, the only real limits on them were caused by technical limitations in the NSA’s hardware. Most of us are familiar with the famous examples, like nationwide phone metadata collection. But it’s the bizarre, obscure leaks that really drive this home. “Optic Nerve”: From 2008-2010 the NSA and GCHQ collected millions of still images from every Yahoo! Messenger webchat stream, and used them to build a massive database for facial recognition. The collection of data had no particular rhyme or reason — i.e., it didn’t target specific users who might be a national security threat. It was just… everything.
Read more of this story at Slashdot.
Source: Slashdot – Looking Back at the Snowden Revelations
Video directed by Chris Principe, edited by Justin Wolfson. Click here for transcript.
A few weeks ago, we asked folks at both the main and fashion-specific Rainbow Six subreddits to share pictures of their Rainbow Six: Siege operators and loadouts. We took some of those submissions and shared them with Ubisoft Presentation Art Director Alex Karpazis to get his expert take on the style and the strategy behind these character choices.
Karpazis has plenty to say about the purely superficial bits of Rainbow Six style, calling out some rocking “Twitch Prime purple hair” in particular. But he also gets into how that style can affect gameplay, as with different gun sights that “obscure different parts of the screen” when trying to make your shot. There’s also some general strategy advice mixed in, especially for people who accidentally kill their hostages with Fuze’s grenade-spreading gadget.

A peek behind the scenes during the shoot.
We also convinced Karpazis to show off his own in-game loadouts and stats, a process he preceded by saying “Nobody is good at Rainbow, including me… Please be gentle, I get it.”
Read 1 remaining paragraphs | Comments
Source: Ars Technica – Video: Ubisoft’s Alex Karpazis rates your Rainbow Six: Siege loadouts

Before they were posh, super spies saving the present-day world, the heroes of Fox’s Kingsman franchise were posh in an old-timey way befitting of an era where parachutes were considered cutting-edge technology. The latest trailer for Matthew Vaughn’s upcoming Kingsmen prequel, The King’s Man, is light in the way of…
Source: io9 – A New King’s Man Trailer Asks ‘What If Downton Abbey Had Super Spies?’

In his 45 years as a shrimp fisherman in south Louisiana, Venice native Acy Cooper has never seen the industry suffer like it has this year. Not after Hurricanes Katrina and Rita in 2005. Not in the years after the BP Deepwater Horizon oil spill in 2010.
Source: Gizmodo – Why the Mississippi River Needs a Bill of Rights
Exim 4.92.3 has been released with a fix for CVE-2019-16928, a heap-based
buffer overflow in string_vformat that could lead to remote code
execution. “The currently known exploit uses a extraordinary long
EHLO string to crash the Exim process that is receiving the message. While
at this mode of operation Exim already dropped its privileges, other paths to
reach the vulnerable code may exist.“
Source: LWN.net – Exim 4.92.3 security release

Bandai Dragon Ball Z Scouters | $12 | Amazon
Source: io9 – Cosplay Is Hard, But Right Now Picking Up This Scouter Will Cost You Fewer Zenni
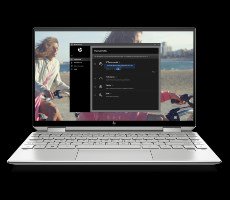
Hewlett-Packard is refreshing its popular Spectre x360 13 with a number of critical upgrades that make it an even more compelling mobile warrior for professionals. Perhaps the biggest change comes with respect to the device’s chassis, which has nipped and tucked to the max.
HP has managed to shrink the Spectre x360 13 by 13 percent compared
Source: Hot Hardware – HP Spectre x360 13 Revamped With Smaller Chassis And 10th Gen Intel Ice Lake CPUs
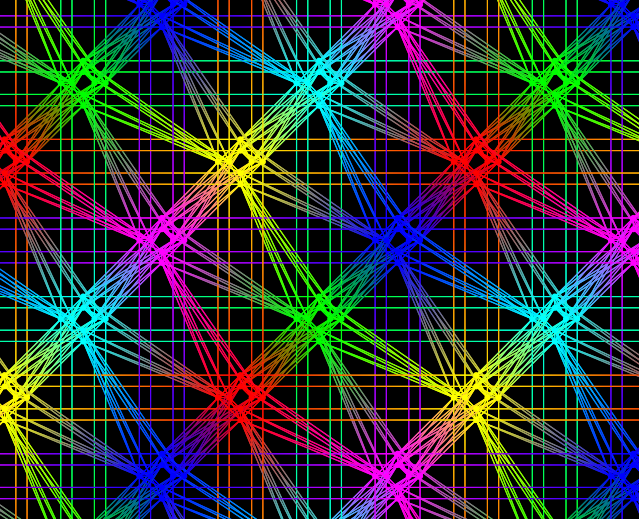
A depiction of the complex topology of the connections among qubits in D-Wave’s next-generation hardware. (credit: D-Wave)
On Tuesday, D-Wave announced the details of its next-generation computation hardware, which it’s calling “Advantage,” and released a set of white papers that describe some of the machine’s performance characteristics. While some of the details of the upcoming system have been revealed earlier, Ars had the chance to sit in on a D-Wave users’ group meeting, which included talks by company VP of Product dDsign, Mark Johnson and Senior Scientist Cathy McGeoch. We also sat down to discuss the hardware with Alan Baratz, D-Wave’s chief product officer. They gave us a sense of what to expect when the machine comes online next year.
D-Wave’s hardware performs a form of computation that’s distinct from the one being pursued by companies like Google, Intel, and IBM. Those companies are attempting to build a gate-based quantum computer that’s able to perform general computation, but they’ve run into known issues with scaling up the number of qubits and limiting the appearance of noise in their computations. D-Wave’s quantum annealer is more limited in the types of problems it can solve, but its design allows the number of qubits to scale up more easily and limits the impact of noise.
It’s easiest to think of a D-Wave as exploring an energy landscape filled with hills and valleys. It specializes in finding the lowest valley in one of these landscapes and avoids getting stuck in a local valley by using quantum effects to “tunnel” through intervening hillsides. That can be used to perform calculations, but only if the calculation can be structured so that it looks like an energy minimization problem.
Read 11 remaining paragraphs | Comments
Source: Ars Technica – D-Wave announces the next generation of its quantum annealer
This is a short dashcam video of a motorist traveling around 70MPH on I-75 near Detroit and clipping a sofa that appears out of nowhere. Thankfully, the driver is fine, the car only suffered some slight wheel well bowing, and the couch was removed from the roadway. Still, somebody really needs to take a course in decorating. I mean if you put the couch there, where are you gonna put the TV? And I don’t even wanna think about the trek to the fridge for another cold one.
Keep going for the video while I speculate if this sofa’s owner also has a fire pit in their bathroom and toilet in the kitchen.
Source: Geekologie – It Came Outta Nowhere!: Dashcam Footage Of Driver Clipping A Couch On Highway At 70MPH

A discounted Eufy Smart Doorbell, Philosophy deals, and a sale on Samsung 8K TVs lead off Monday’s best deals from around the web.
Source: LifeHacker – Monday’s Best Deals: Samsung 8K TVs, Kohler Fixtures, Rubik’s Cube, and More
The concept of mobile gaming is still a relatively new phenomenon. The idea that a user can have a smartphone dedicated to gaming that isn’t in of itself a console or handheld platform from Nintendo seems very odd – here’s a device that does everything a phone can do, as well as play the same games, so what makes it a “Gaming Phone”, especially if it has almost the same hardware inside? ASUS’s new ROG Phone II, designed under its Republic of Gamers brand, is ultimately a product designed to showcase that there are things you can do with a phone to make it more gaming focused. We take the device (and some of its accessories) for a spin.
Source: AnandTech – The ASUS ROG Phone II Review: Mobile Gaming First, Phone Second

Chinese police used a drone to track down a convicted human trafficker 17 years after he escaped from jail.
Source: Gizmodo – Police Drone Finds Fugitive Living in Cave After 17 Years on the Run