It feels as though Google Chrome has been around forever, but it’s actually still just a teenager: The browser launched back in 2008, originally just for Windows—though it’s now made its way to macOS, Linux, and mobile devices too of course. It’s a powerhouse of a browser that is more widely used than any other.
In the 18 years since its release, Chrome has changed a lot: A host of features have been added and taken away down the years, and it’s very possible that you don’t know everything that Chrome can do, even if you use it every day. Here are my favorite hacks for Chrome, covering everything from casting tabs to playing audio and video.
Change the look and feel of Google Chrome
If you’ve always stuck with the ‘out of the box’ Chrome aesthetic, you might not be aware that it’s relatively simple to change up the theme of the browser—which covers the colors of menus and tabs, as well as what you see on the new tab page. To see the available options, open up a new tab, then click the Customize Chrome button (lower right).
You can apply any of the color themes just by clicking on them, or set up your own colors by clicking the color picker (the little pipette icon). For a more significant visual overhaul, click Change theme: You’ll then see a range of options created and curated by Google. Click Chrome Web Store to see more official and third-party themes you can install.
Claw back some RAM from Chrome
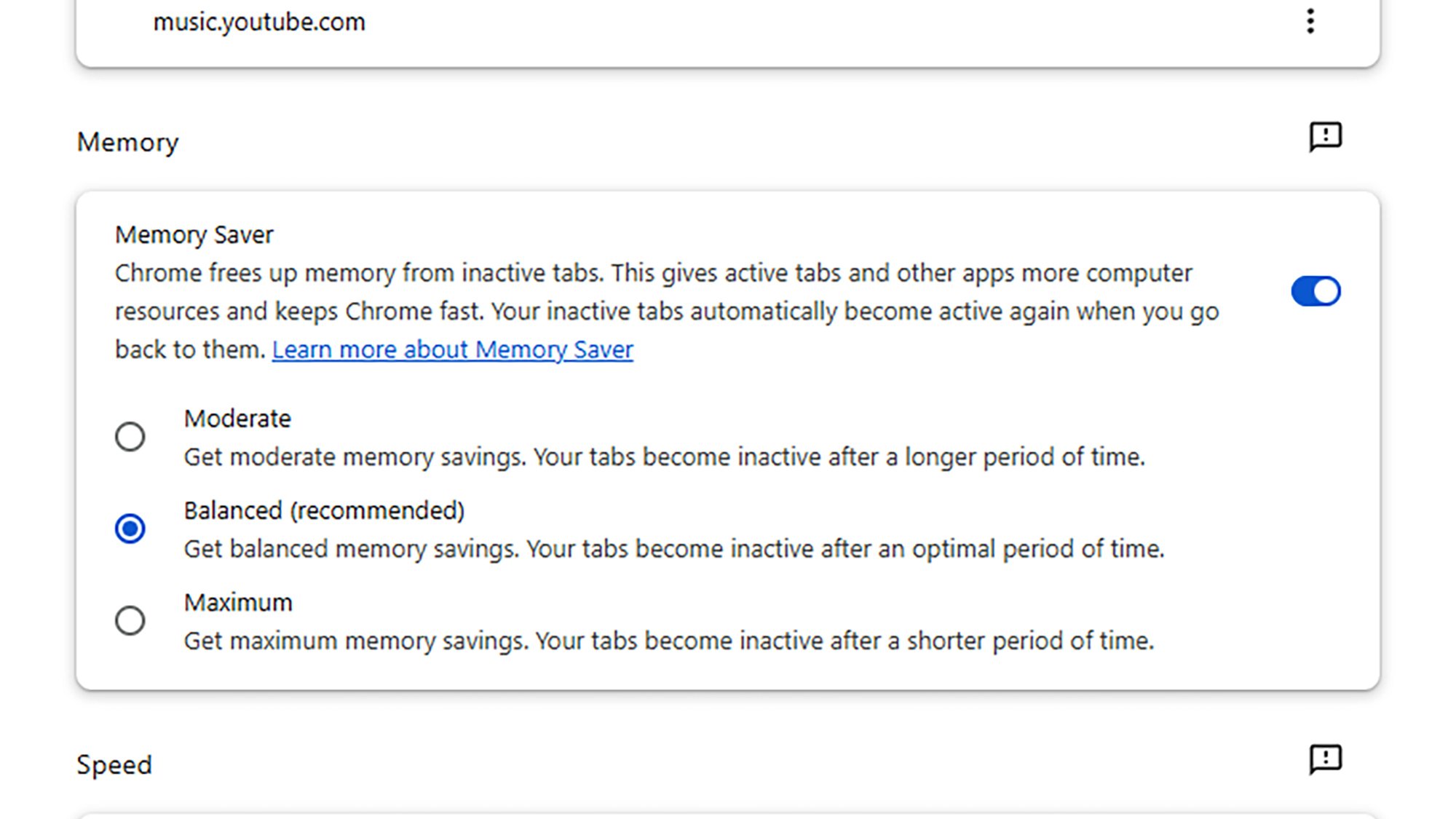
Credit: Lifehacker
It’s fair to say Chrome doesn’t have the best reputation for efficient RAM usage, but you can get some of it back. In any tab, click the three dots (top right), then choose Settings > Performance, and activate the Memory Saver option. As Google explains, this will put tabs you’ve not used in a while in an inactive state, and recover some RAM from them.
Put your tabs up on a big screen
It’s not a Chrome feature that gets much attention, but you can cast tabs wireless to a big screen via Google TV or Chromecast devices. It’s useful for everything from music streaming to slide presentations, though the latency is usually too high for video playback (and bear in mind that YouTube, for example, has its own casting button for this).
With a tab open in Chrome, click the three dots in the top right corner, then choose Cast, save and share > Cast. You’ll then be asked to choose the device to cast to (which must be on the same wifi network of course). Via the Sources button, you can choose to cast just the tab you’re in, or your entire Windows or macOS desktop, including Google Chrome.
Switch up your search engine
Credit: Lifehacker
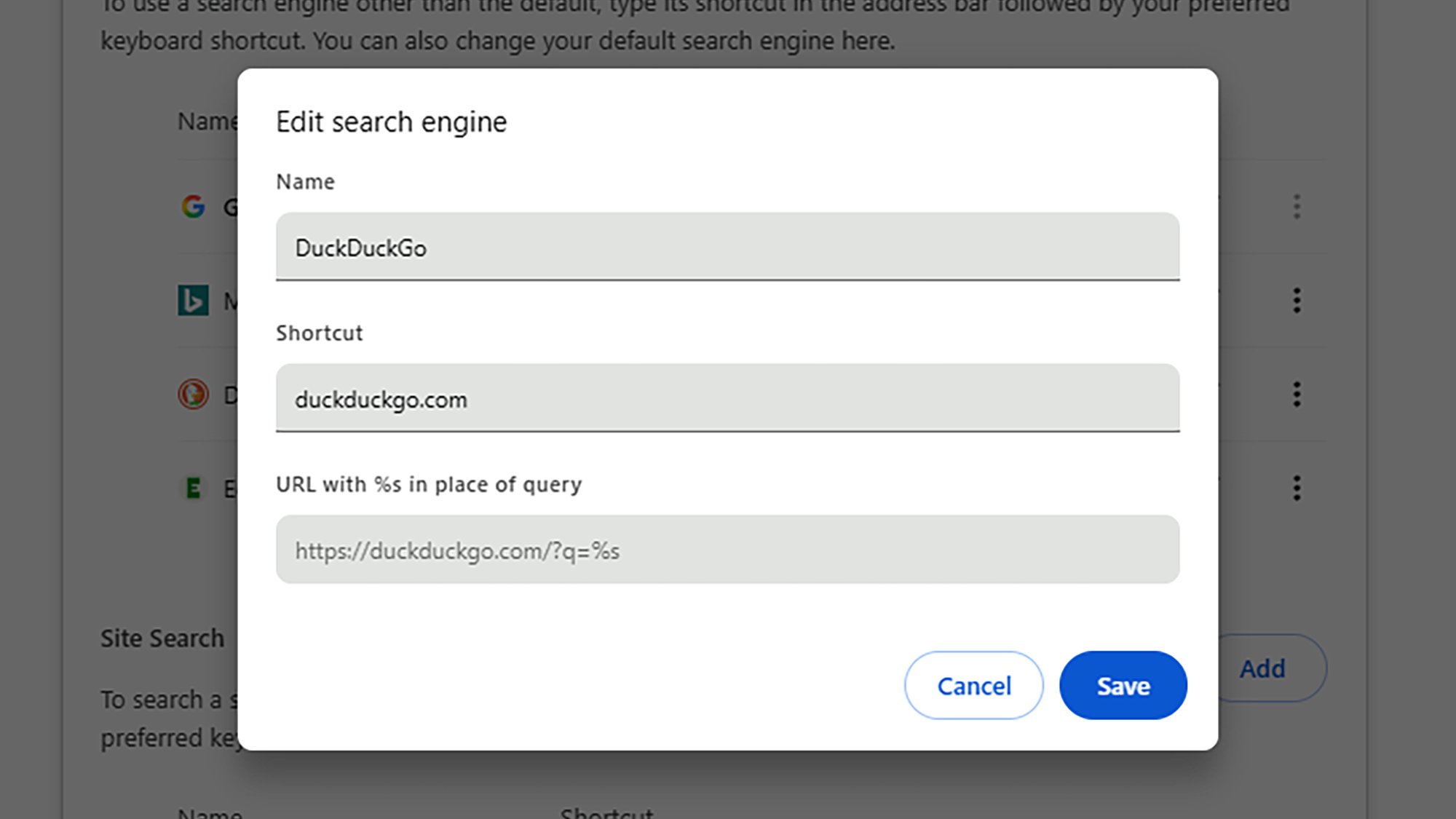
Just because you use Google Chrome doesn’t mean you have to use Google Search—maybe you want to switch to a privacy-first alternative, like DuckDuckGo. To set up search engines in Chrome and change the default one, click the three dots in the top right corner of any tab, then choose Settings, and open the Search engine page.
Use the Add button to add new search engines, the pencil icons on the right to edit their details, and the three dots on the right to set which one is used by default (when you type some search terms into the Chrome address bar). Each search engine can also have a shortcut: Type the shortcut into the address bar to run a search using that specific site.
Group your tabs together
Tab grouping can make it much easier to manage the myriad tabs you’ve got open in every single session—these groups can be moved and closed and saved all together, so you could set up different groups for different research projects, for example, or for different tasks in the browser (maybe one for work-related browsing and another for shopping).
The easiest way to get started with tab groups in Chrome is to right click on a tab header and pick Add tab to new group from the pop-up menu. Give your tab a name and color, and if you then right-click on other tab headers, you’ll be able to add them to the group (or create a new one). Right-click on the headers of grouped tabs to access further options.
Switch between user profiles
Credit: Lifehacker
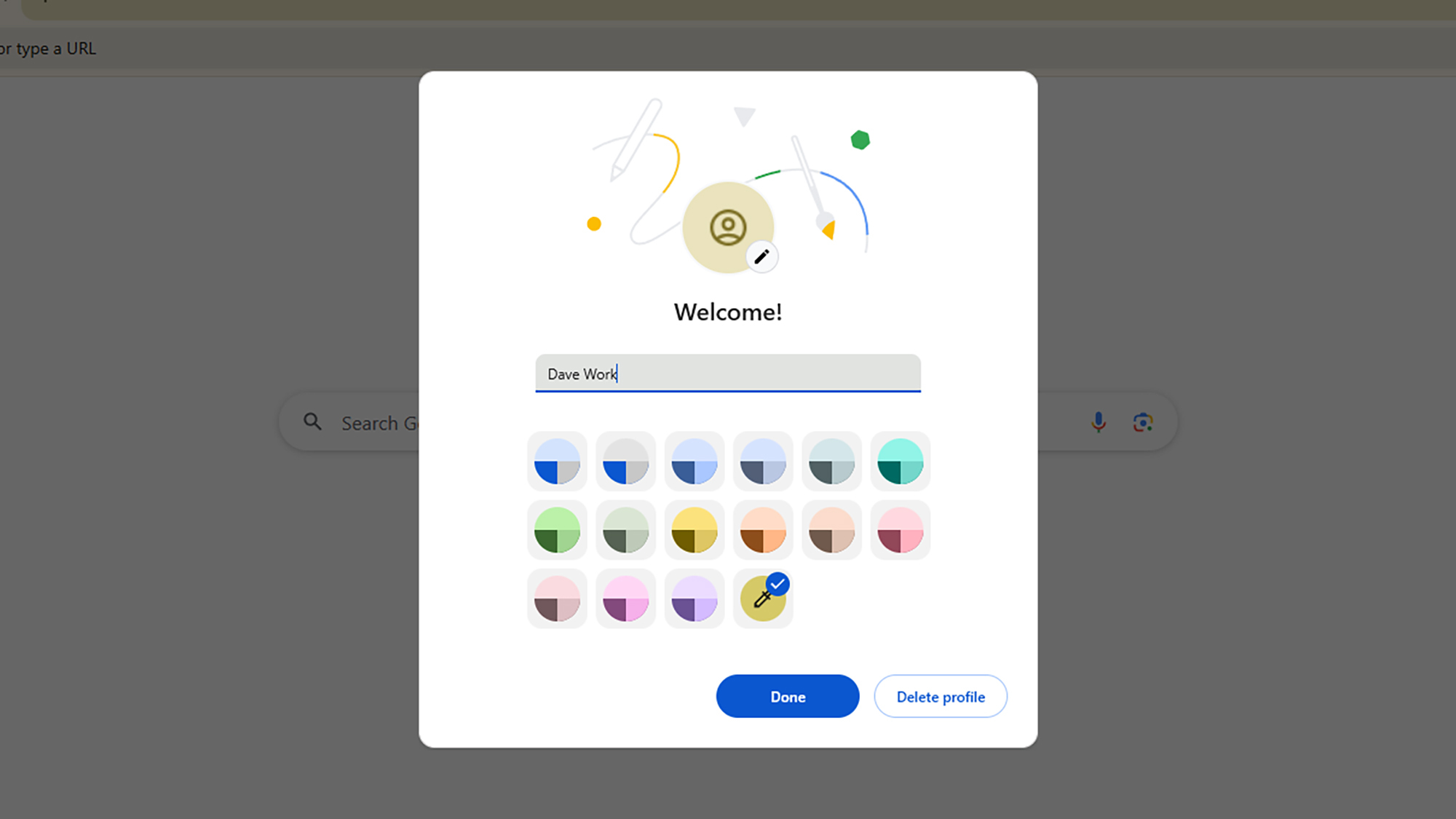
User profiles are a hugely powerful Chrome capability that more people should know about: It lets you split your browsing into work and personal categories, for example, (and separate Google accounts, if needed). It means that logins, browsing history, and all the other data that gets stored in Chrome don’t all get lumped together in one place.
So, you could use your work profile for the day, and then switch to your personal profile at night—making it easier to access your Netflix login and Amazon shopping history, for example. To get started with profiles, click your current profile avatar (in the top right corner, next to the three dots), then choose Add Chrome profile from the menu.
Edit webpages with Tampermonkey
If you’re prepared to invest some time and effort into your Chrome hacking, give the Tampermonkey extension a look (it’s actually available for several browsers, not just Chrome). The tool lets you inject your own custom code to modify the websites you’re looking at, so you can alter the appearance or even the functionality of pages.
You could remove distractions from a page, for example, add your own keyboard shortcuts for navigation, or insert new buttons for sharing links on social media. We don’t have the space for a full tutorial here, but if you head to the Tampermonkey website you’ll find a wealth of help to get you started, plus some links to user script repositories on the web.
Install web apps in Windows or macOS
Credit: Lifehacker
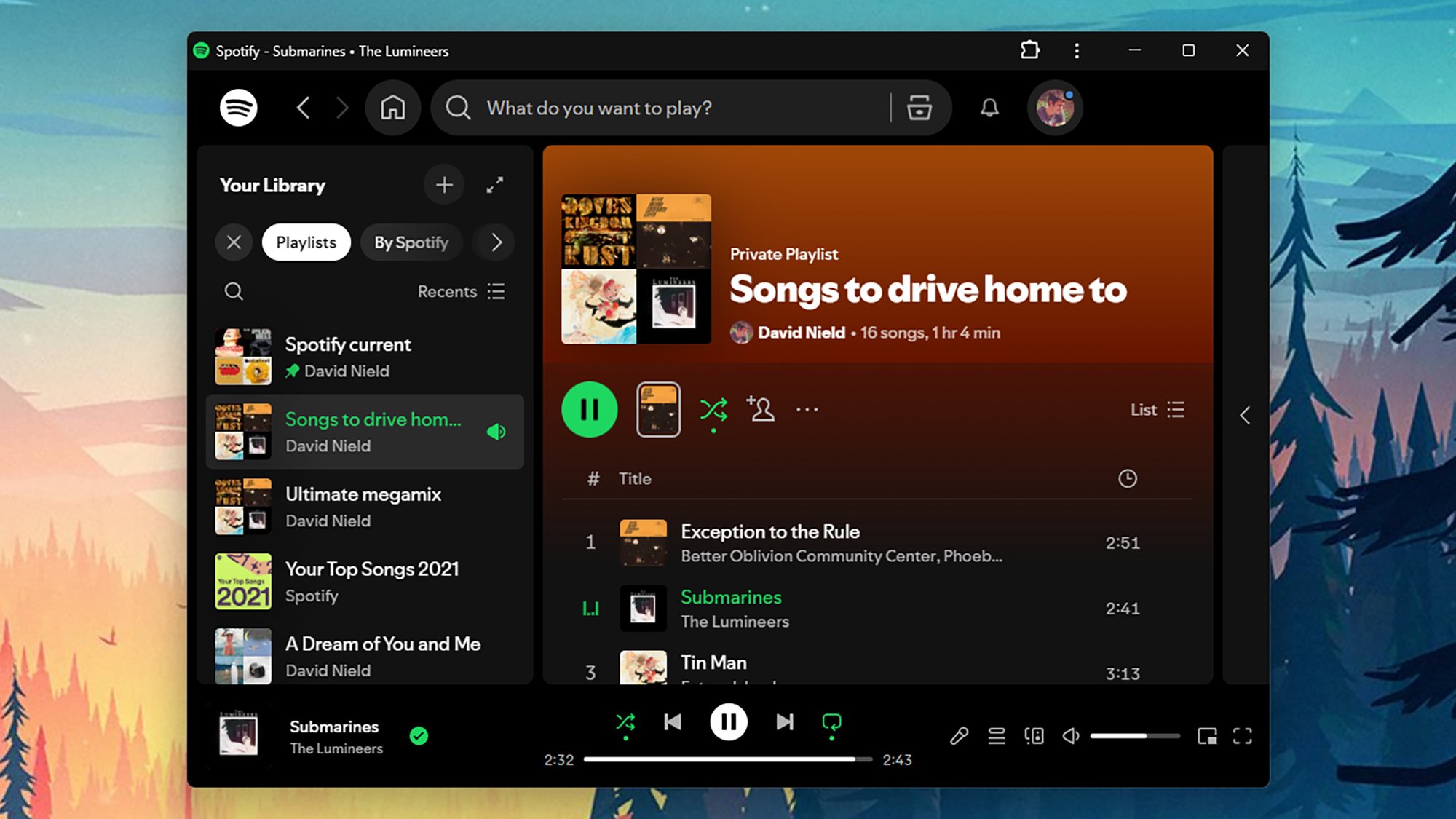
There are plenty of powerful web apps you can get at through Chrome—Slack, Gmail, Spotify—and Google’s browser lets you set these up as if they were desktop apps in Windows or macOS. You can get a shortcut straight to the app on the Windows taskbar or macOS dock, and when you launch it, it appears in its own distinct desktop window.
With the web app open in Chrome, click the three dots (top right), then choose Cast, save and share > Install page as app. You’ll then be asked to give your new app a name, and click Install to confirm. The app launches right away, and you can then organize it into your Windows or macOS system as you want (by pinning it to the taskbar, for example).
Run a check for safety and privacy
Chrome comes with a built-in Safety Check that runs an audit on passwords, security updates, third-party extensions, and more. You can find the Safety Check screen by clicking the three dots to the top right of any tab, then choosing Settings > Privacy and security: As well as running the check, you can follow the recommended actions.
Use Chrome to preview files and preview media
Credit: Lifehacker
Google Chrome can handle more than webpages: It’s also able to open up PDF documents, and image, video, and audio files saved in common formats (like MP3 or MOV). Just drag a file into an empty tab to open it, or associate the file type with Chrome in Windows or macOS (which means it’ll automatically open in the browser when you double-click on it).
Chrome isn’t the most advanced PDF editor or video player you’re ever going to see, but it’s a quick and easy way of opening up local files without having to launch an entirely separate program each time. You could use this alongside the Split View feature, for example, to watch a video stored on your system while making notes in Google Docs.